By B.N. Frank
By B.N. Frank
Research has already determined that there are significant health risks associated with exposure to Electromagnetic Fields (aka “Electrosmog”) as well as wireless “Wi-Fi” radiation from cell phones, activity trackers and other wearables, utility “Smart” Meters and other common wireless sources. Got pets? Exposure can affect them too.
Manufacturers are required to provide warnings about radiation emissions from their products; however, these warnings aren’t necessarily easy to find or understand. There are government agencies worldwide that have taken steps to warn and protect their citizens from radiation exposure (see 1, 2). Unfortunately, this doesn’t include agencies in the in the U.S. despite lawsuits and petitions (see 1, 2, 3, 4). However, the Food and Drug Administration (FDA), the American Heart Association, and Apple have warned that some electronic and/or wireless devices can cause dangerous and sometimes deadly interference issues with cardio defibrillators, pacemakers, and other medical implants.
Thanks to Environmental Health Trust for creating a web page with “fine print warnings” of numerous common wireless radiation-emitting products. Here’s one of many examples:
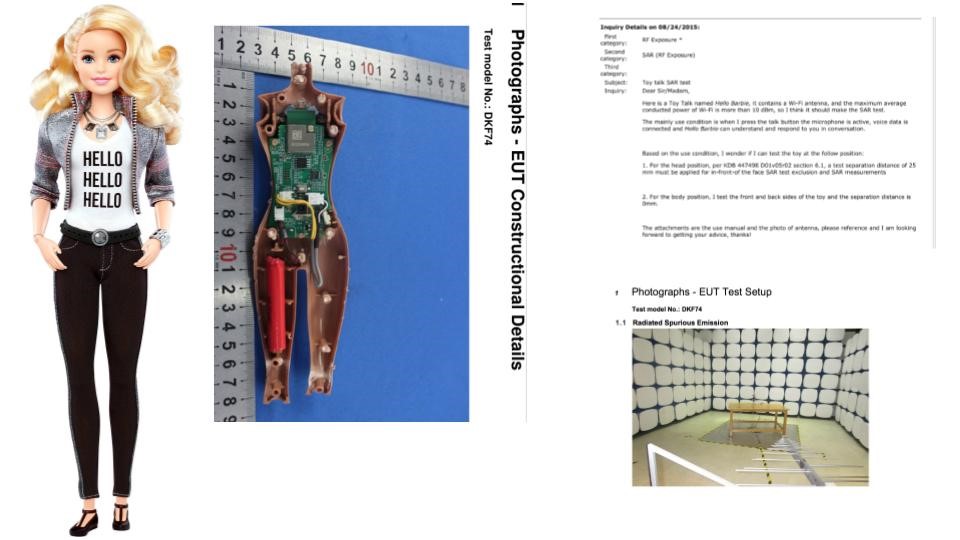
Wi-Fi Barbie
“End user must follow the specific operating instructions for satisfying RF exposure compliance. This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter. The portable device is designed to meet the requirements for exposure to radio waves established by the Federal Communications Commission (USA). These requirements set a SAR limit of 1.6 W/kg averaged over one gram of tissue. The highest SAR value reported under this standard during product certification for use when properly worn on the body.”
Environmental Health Trust offers additional webpages with information about “fine print” warnings as well (see 1, 2). Of course, privacy and security experts have also warned for years about manufacturers’ data collection (and sharing) via wireless “Smart” products as well as their vulnerability to hackers (see 1, 2, 3, 4, 5, 6, 7).